DKIM is a technological advancement in the field of email security. SPF prevents non-authorized servers from sending emails, but it does not prevent all attempts at spoofing. This is where our next level of security comes into play.
DKIM or Domain Keys Identified Mail aids to the security of the email as it adds a digital signature to every outgoing message, allowing receiving servers to verify that the message came from your organization. It ensures that the content of the email remains untampered/compromised and can be trusted.
DKIM record verification is enabled by cryptographic authentication.
To setup DKIM for your email, you will need DKIM records that exists in the DNS records just like SPF.
How does DKIM Record look like?
A DKIM record, which is a modified TXT record, is added to the DNS records of the sending domain by the domain owner. This TXT record will include a public key that receiving mail servers will use to verify a message’s signature. The key is frequently provided to you by the organisation sending your email.
$ dig dkim._domainkey.0xcardinal.com TXT
...
;; QUESTION SECTION:
;dkim._domainkey.0xcardinal.com. IN TXT
;; ANSWER SECTION:
dkim._domainkey.0xcardinal.com. 3481 IN TXT "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC2GzACcNkgHJcEyo7o9Wme2GNOGVXEv/aaj4pxgnT7HfCxcl6uBG1am/in7WGuPGNLKVcyFiuXww/WA64fOfrlwqCu0zCzt1sdQjnEHMUzVKwTGwXLkx/7AWo0T2ArAAt5n98m4NNtK7oi63CxaEtG86L1Serln66PAoYHUw16fQIDAQAB"
...
How does DKIM work?
A very cool infographic that helps in understanding the flow -
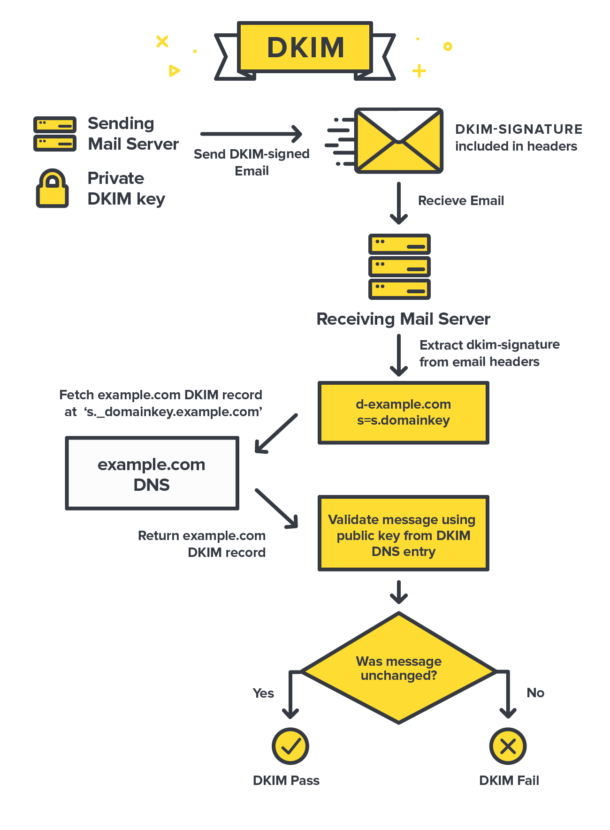 Source:
https://postmarkapp.com
Source:
https://postmarkapp.com
Validating the DKIM Record (If the mail is untampered) has four parts to it -
- The sender identifies what fields (“from” address, subject, body, etc.) needs to be included in the DKIM signature.
- The sender’s email platform creates a hash of the text fields included in the DKIM Signature, then it is encrypted with the private key of the sender.
- Email gateway, finds the public key and validate it against the private key, then it is decrypted back to the original hash string.
- The receiver generates it’s own hash based on the fields mentioned in the DKIM record and compare with the hash sent by the sender.
Anatomy of DKIM Signature
DKIM Signature is a header that is added to email messages. The header contains values that enable a receiving mail server to validate the email message by retrieving the sender’s DKIM key and using it to validate the encrypted signature.
E.g. -
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=dkim; d=0xcardinal.com;
h=From:Date:Subject:MIME-Version:Content-Type:Content-Transfer-Encoding:To:Message-ID;
i=sign@0xcardinal.com; bh=vYFvy46eesUDGJ45hyBTH30JfN4=;
b=iHeFQ+7rCiSQs3DPjR2eUSZSv4i/Kp+sipURfVH7BGf+SxcwOkX7X8R1RVObMQsFcbIxnrq7Ba2QCf0YZlL9iqJf32V+baDI8IykuDztuoNUF2Kk0pawZkbSPNHYRtLxV2CTOtc+x4eIeSeYptaiu7g7GupekLZ2DE1ODHhuP4I=
Here’s what each header means -
DKIM-Signature: v=1;- The version of DKIM used. Always the first part of the Signature.a=rsa-sha1;- Algorithm used to generate hash for the public/private keys.c=relaxed/relaxed;- Sets what can be modified in the signature. Set the canonicalization posture of the domain. There are two values for this -simple- Does not allow any changerelaxed- Allow common changes like whitespaces and header line-wrapping.
s=dkim;- DKIM Selector for the Public Key for verification.d=0xcardinal.com;- Email domain that signed the message.From:Date:Subject:MIME-Version:Content-Type:Content-Transfer-Encoding:To:Message-ID;- Headers included with the message when it was cryptographically signed.[email protected]- Identity of the signer.bh=vYFvy46eesUDGJ45hyBTH30JfN4=;- Value of the body hash generated before the message headers are signed.b=iHeFQ+7rCiSQs3DPjR2eUSZSv4i/Kp+sipURfVH7BGf+SxcwOkX7X8R1RVObMQsFcbIxnrq7Ba2QCf0YZlL9iqJf32V+baDI8IykuDztuoNUF2Kk0pawZkbSPNHYRtLxV2CTOtc+x4eIeSeYptaiu7g7GupekLZ2DE1ODHhuP4I=- The cryptographic sign of all the information from theDKIM-Signaturefield.
Now, we know how to make sense of the DKIM records.
Problems?
Receivers benefit from a DKIM record because it alerts them to emails that may contain malicious or spam content. It also ensures that the data in the DKIM signature was not altered in transit. However, because DKIM is more difficult to implement, fewer senders have adopted it. Furthermore, DKIM does nothing to prevent email spoofing of the visible parts of an email’s “from” field, such as the email address, display name, and domain. As a result, DKIM, like SPF, is insufficient to protect an organization from sophisticated phishing attacks on its own.
Using DKIM along with DMARC - improves the fallbacks it has. Will cover DMARC in subsequent blog.
Stay Tuned! See you till then 👋
References?
These are a few blogs that helped me curate this content and try to present it in easy manner -
- https://www.sparkpost.com/resources/email-explained/dkim-domainkeys-identified-mail/
- https://dmarcian.com/what-is-dkim/
- https://postmarkapp.com/guides/dkim
- https://www.dmarcanalyzer.com/how-to-validate-a-domainkey-dkim-record/
- https://www.proofpoint.com/us/threat-reference/dkim
Thanks🙏
